Well, it’s the New Year, and I wish you all the best for a fantastic 2013! I can’t believe my last post was in November! And it’s already the end of January! So I thought I’d get in quickly with my two pennies worth of crystal ball gazing before it becomes unfashionable... What did we learn from 2012? Are there any interesting market trends? How does it affect security? What is the current state of information security and how is it shaping up? Are we getting any better? If any of these questions spark your interest of if you’d just like to see if my Nostradamus impression has something in it, read on...
Looking back...
In the 2012 Verizon Data Breach Investigation report, we all noticed a slight change in the nature of data breaches experienced in the past year:
Payment card information represented 48% of all breaches in 2011, but unlike previous years, it was not a runaway winner.
Whilst payment cards retained the title of “most stolen”, the dubious honour of “largest hauls” now firmly belongs to other types of personal information, including name, e-mail, national ID, etc. (95%)
And of course, authentication credentials were a close second 42% in the current dataset.
And the notable increase in the number of data breaches experienced at the beginning of 2012 remained on the upwards path, giving us a whopping 37.2% increase at the end of the year (and already 52 breaches in 2013!):
 |
| source: datalossdb.org 28th January 2013 |
In the very same Verizon report, we saw that 84% of breached organisations didn’t detect the breach themselves. It is also interesting to note that for those organisations that self-detected, attackers only had a quarter of the time in which to inflict damage compared to those who remained unaware. So what of the buzzwords that we had to live with throughout 2012: cloud exploits, mobile device attacks, cyberwar... Were those the causes of most breaches? Well, let’s see...
A bit of debunking...
For 2013, The Verizon RISK team don’t foresee the failure of an organisation’s cloud technology or configuration as being the root cause of a breach, but a service provider could increase the likelihood of a breach by failing to take appropriate actions or taking inappropriate ones (sub-text: your cloud = your problem, nothing new there).
Similarly, Verizon believe that lost & stolen (and unencrypted) mobile devices will continue to far exceed hacks and malware (subtext: negligence is still a problem).
They also project that attacks on mobile devices by the criminal world will follow closely the push to mobile payments in the business & consumer world and whilst we might notice this shift towards the end of 2013, mobile devices as a breach vector in larger enterprises will lag beyond 2013 (subtext: new tech = new risks, be prepared).
And as for targeted attacks from adversaries motivated by espionage & hacktivism, as I mentioned in previous articles, these attacks are totally linked to the types of organisations targeted and they will continue to occur, so appropriate risk management must be in place (and for such organisations, such as those in critical infrastructure, this remains a priority).
So, what’s really happening?
Going back to mainstream and mass market, the Verizon 2013 predictions for 2013 top three concerns are surprisingly unexciting (in a good way...):
- Authentication Failures/ Attacks (90% probability)
- Web Application Exploits (75% probability)
- Social Engineering
Here we are, this all comes down to basic security lapses, negligence and common sense and this is not different from what we have observed over the past four years.
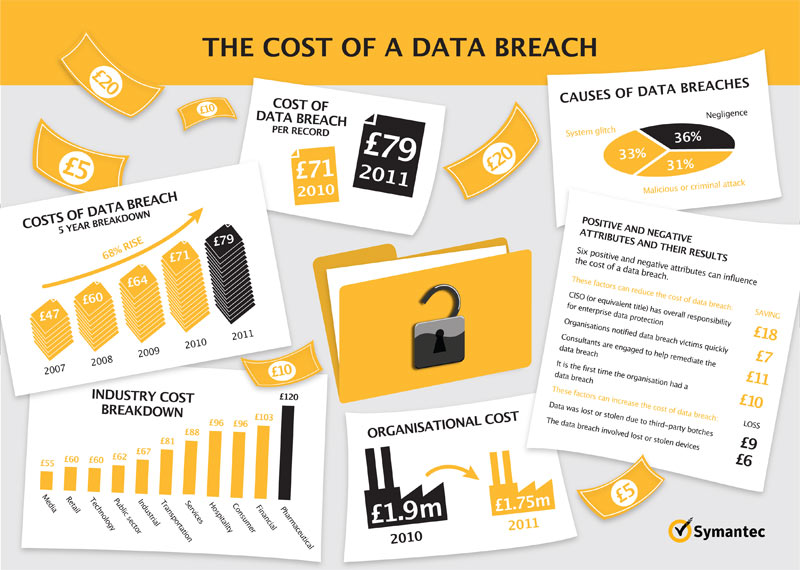
But, we have also noticed an interesting change in the last year, as summarised in a recent Symantec survey (Cost of a Data Breach Study, United Kingdom, March 2012):
The findings reveal that fewer records are being lost in these breaches and that there is less customer churn. So whilst the cost of a data breach has increased from £71 in 2010 to £79 in 2011, the total organisational cost has reduced from £1.9m to £1.75m. For the first time in years, this small 8% decline suggests that organisations represented in this study improved their performance in both preparing for and responding to a data breach. So maybe the message on incident response is getting through...
To recap, what are we faced with?
- Data breaches have become a statistical certainty and third party breaches continue to increase...
- Information security is no longer just about deploying controls...
- Effective incident response is a priority...
- Social media usage has exacerbated exposure...
- Cloud computing demand has increased risk...
- Mobile/alternative payments have generated friction between marketing, business development, IT and security...
- Regulations have become tougher...
Some market trends...
This new growth and threat landscape has in turn had a very interesting effect on the market:
- The multi-factor authentication market is forecast to grow to $5.45 billion by 2017;
- Gartner predicts that cloud Identity & Access Management (IAM) will grow 500% by 2015;
- The global Mobile Device Management (MDM) Enterprise Software market forecast to grow at a CAGR of 7.8% over the period 2010-2014;
- The global mobile security market, projected to have reached $1.6 billion in 2012, is expected to continue its growth spike in 2013, according to a Visiongain report.
More regulations...
On 23rd February 2013, the European Commission will propose a new obligation for security breach notifications for the energy, transport, banking and financial sectors,” said an official working at the Commission's digital agenda department. It also confirmed plans to extend security breach notifications to new industries, other than telecommunication companies and internet firms which in Europe are already subject to reporting obligations.
And I couldn’t really write about information security and not mention China, so here goes: on 28th December, the Standing Committee of the National People’s Congress (NPC) of the People’s Republic of China passed a resolution relating to strengthening the protection of information on the internet. The regulations contain significant and far reaching requirements applicable to the collection and processing of information via the internet. . And so have Singapore.
And of course, the Information Commissioner’s Office has been very active in 2012. To the point that on 24th January 2013, nearly two years after the Sony breach, the ICO fined them £250K for breach of the DPA.
Mobile and social...
- 2013 will see more focus on social media, and as social media usage explodes, what risks should we consider? (see my previous blog post on the subject)
- As mobile device pervasiveness increases, so will the attacks... How prepared are we?
- As mobile payment acceptance emerges, what are the security implications?...
- The monetisation of social networks introduces new risks, do we know what they are?...
- Businesses are now looking at social commerce. We saw the emergence of f-commerce, the rise of pinterest and now shoppable videos, are we ready to support this payment revolution?
The current conditions have implications on the role of the CIO, who is now required to exhibit the following skills:
- IT Security & Compliance
- IT Project Management
- Partner/ IT Vendor Management
- Corporate Finance
- Enterprise Data Management
- Legal Expertise
A bit of a tall order... Increasingly, the CISO has to compete for investment with their marketing and business development colleagues... Below are some tips that enable them to put their best foot forward (Source: darkREADING, November 2012, 7 Risk Management Priorities For 2013):
- Getting Quantitative (Measure Performance)
- Using GRC To Improve Business & IT Processes
- Third Party Risk Management
- Address Human Risks
- Continuous Monitoring
- Speaking The Language
- Incident Preparedness
I’ve been doing these for the past three years, and so far, I think I haven’t been off the mark, so here goes for this year and in reverse order:
9. Mobile: whether it’s BYOD or mobile payments, now is the time to prepare for the surge. Factors to consider are:
Mobile device attacks
Mobile Device Management
Mobile payments
Social mobile payments
Mobile payment acceptance
8. Social Media:
Social Media Risk (see my previous post)
Social Media Engagement
Social Media Servicing
Marketing drive
Finance pressure
Alternative payments
Monetisation of social networks
Social Engineering (see my previous post)
New social platforms
7. Laws & Regulations:
EU Data Protection Laws
Disclosure Laws
PCI DSS
All Privacy Laws
Cloud implications (if you have time, excellent report from Stanford Technology Law Review)
Legal Counsel
6. Incident Response:
84% of organisations were notified of a breach by external entities.
Containing the size of the breach and improving responsiveness can result in lower organisational costs by £7 per compromised record.
(see my previous posts on incident response here and here).
5. Enterprise GRC (Governance Risk & Compliance):
Laws/ Regulations tracking
Enterprise Asset Management
Security & Compliance
Automation
Economies of scale
Process efficiencies
Continuous monitoring
Performance measurement (see my previous post)
Finance KPIs
New social platforms
4. Third Parties:
Cloud security (See my previous posts here and here)
Big data
Merchant agents
Card scheme mandates (for those in payments)
Data breaches caused by third parties can increase the overall cost by £9 per compromised record
3. Authentication:(see here, I'm not alone...)
Credentials breaches
Authentication failures
Multi-factor authentication
Identity & Access Management
Behavioural analysis
Fraud management
2. Awareness & Education:
Having a CISO with overall responsibility for enterprise data protection can reduce the average cost of a data breach by as much as £18 per compromised record.
Data breaches resulting from lost/stolen devices can increase the overall cost by £6 per compromised record.
Speaking the language (finance, law, marketing, business development, etc.)
Human risks
36% breaches were due to negligence.
Social engineering
1. Risk Management: of course, if you get this one right, you can address all the others in a way that puts your business back in control of its destiny (and security!)
Corporate finance
Regulations
Existing risks
Emerging risks
Emerging technologies
Business growth
And everything else to deploy an effective and convergent business framework... (see my previous posts here and here).
For those who know me, this list will be no surprise, especially the top three... If you’d like to see a PowerPoint version of this post, try this.
Of course, now I look forward to the 2013 Verizon DBIR :), but before that, you could look at my post on 2013 breach statistics.
Until next time...
neirajones


This is good listing with solid reminders in each category. Almost avoids the Escherial recursive occlusion of the others ;o)
ReplyDeleteHi Danny! Tee hee :) almost...
ReplyDeleteNeira - Very well thought out and comprehensive ! Thanks William
ReplyDeleteThanks for the feedback William! :)
ReplyDeleteAwesome insight Neira, and so much better to see it presented in person yesterday!
ReplyDeleteThank you
Phil
Really nice and interesting post. Keep posting. Thanks for sharing.
ReplyDelete360DigiTMG
I am genuinely thankful to the holder of this web page who has shared this wonderful paragraph at this place
ReplyDeleteartificial intelligence courses in Guwahati