If in doubt, classify...
As in 2013, the 2014 report uses the North American Industry Classification System (NAICS), which is as good as any for introducing consistency, but will perhaps need a bit of translation and adjustment from the 2013 report... I have graphically represented the tabular information given on page 6 of the report and we can make the following observations (click on graph to enlarge):
The graph on the left is for incidents reported, which shows that the public sector is perhaps a bit more trigger happy in terms of incident reporting (the DBIR cites the US agency reporting requirements, but here in the UK we experience the same with the ICO reporting on the public sector which seems to be more stringent). The graph on the right shows confirmed data breaches and the two should be looked at in conjunction.
Even if we take above into account, the public sector was still the second largest sector affected in 2013, after financial services which retains its top position from 2012, closely followed by Retail and Accommodation. And similarly to 2013, Agriculture seems to be the safest sector from cybercrime...
The new top 4 sectors affected are: Financial Services, Public Sector (new entrant), Retail and Accommodation. Manufacturing, whilst still worthy of note, has reduced both in absolute and percentage terms compared to 2013. And as we’re talking about sector split, it is useful to see the comparison between 2012 and 2013 (click on graph to enlarge):
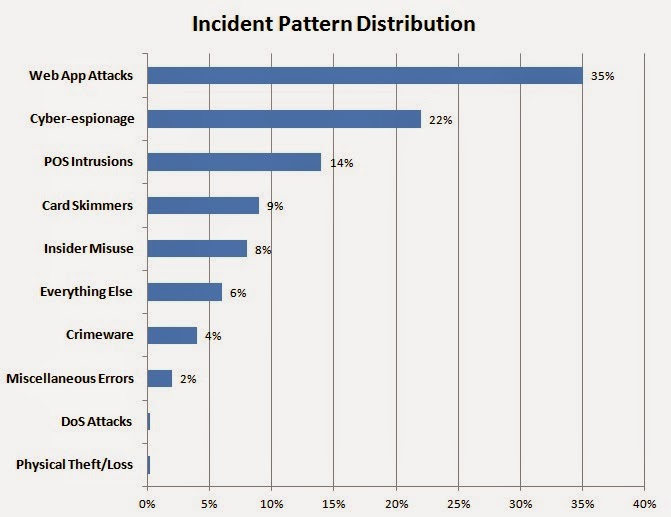
Nine out of ten of all breaches can be described by nine basic patterns...
The 2013 DBIR left us with the exciting prospect that we might be “able to reduce the majority of attacks by focusing on a handful of attack patterns”, and yes, the 2014 DBIR does just that, by reducing the attack patterns to the following nine (click on graph to enlarge):
Again, no surprise there, web application attacks still top of the list and POS intrusions & Card Skimmers have reduced in relative terms to that exhibited in previous years. This trend, IMHO, will continue to accentuate as the US migrates towards EMV (Chip & PIN), and criminals turn their attention to e-commerce more and more (including the expected growth of mobile commerce). Indeed this is confirmed on Figure 20 page 16 of the report. Cyber-espionage is also on the rise from previous years and I am sure my commentary is not needed as to why that is...
Let’s dig deeper...
However, as every professional worth their salt will know, one size very rarely fits all, and therefore the 2014 DBIR goes on to examining how the various attack patterns fit into each industry sector, which I have summarised for you below (in bracket the NAIC number) only listing the key attack patterns for each sector and allocating them in a simple grouping...
Those that should really concentrate on giving their staff more generic security training and beef up on insider fraud prevention measures (including data loss prevention), effective access management as well as device encryption and retention/disposal policies (subtitle: Oops, I did it again...):
- Healthcare [62]: Theft/Loss (46%), %), Insider Misuse (15%), Miscellaneous Errors (12%)
- Administrative [56]: Miscellaneous Errors (43%), Insider Misuse (27%), Theft/Loss (12%)
- Real Estate [53]: Insider Misuse (37%), Miscellaneous Errors (20%), Theft/Loss (13%)
- Public Sector [92]: Miscellaneous Errors (34%), Insider Misuse (24%), Theft/Loss (19%)
- Mining [21]: Insider Misuse (25%), Theft/Loss (10%)
- Education [61]: Miscellaneous Errors (20%), Theft/Loss (15%)
- Transportation [48 49]: Insider Misuse (16%)
- Construction [23]: Insider Misuse (13%), Theft/Loss (13%)
- Entertainment [71]: Miscellaneous Errors (12%)
- Trade [42]: Miscellaneous Errors (9%)
- Accommodation [72]: Insider Misuse (8%)
Those that should really concentrate on application security, perimeter protection, intrusion prevention and outbound connections:
- Information [51]: Web Application Attack (41%), Crimeware (31%), Denial of Service (9%)
- Utilities [22]: Web Application Attack (38%), Crimeware (31%), Denial of Service (14%)
- Finance [52]: Web Application Attack (27%), Denial of Service (26%), Payment Card Skimmer (22%)
- Professional [54]: Denial of Service (37%), Cyber Espionage (29%), Web Application Attack (9%)
- Retail [44 45]: Denial of Service (33%), POS Intrusion (21%), Web Application Attack (10%)
- Manufacturing [31 32 33]: Denial of Service (24%), Web Application Attack (14%)
- Education [61]: Web Application Attack (19%),
- Management [55]: Denial of Service (44%), Web Application Attack (11%), Payment Card Skimmer (11%)
Those that should really concentrate on information asset protection to prevent IP Theft, focus on not being the weakest link in their value chain (as this endangers their customers) and on training their staff on the dangers of ID Theft through social engineering as well as putting measures in place to protect themselves from crimeware:
- Mining [21]: Cyber Espionage (40%), Insider Misuse (25%), Theft/Loss (10%)
- Construction [23]: Crimeware (33%), Cyber Espionage (13%), Insider Misuse (13%), Theft/Loss (13%)
- Information [51]: Crimeware (31%)
- Utilities [22]: Crimeware (31%)
- Transportation [48 49]: Cyber Espionage (24%), Web Application Attack (15%), Crimeware (15%)
- Public Sector [92]: Crimeware (21%)
- Professional [54]: Cyber Espionage (29%), Web Application Attack (9%)
- Manufacturing [31 32 33]: Cyber Espionage (30%), Web Application Attack (14%)
- Management [55]: Web Application Attack (11%), Cyber Espionage (11%)
- Trade [42]: Crimeware (9%)
Those that should really concentrate on payment security:
- Accommodation [72]: POS Intrusion (75%)
- Finance [52]: Web Application Attack (27%), Payment Card Skimmer (22%)
- Retail [44 45]: POS Intrusion (21%), Web Application Attack (10%)
- Management [55]: Web Application Attack (11%), Payment Card Skimmer (11%)
And are we better at incident response?...
Well, sad news here, and whilst there is not much data in the report apart from the generic graph on page 12 (Figure 13), we can see that the gap continues to widen between “how long it takes the attacker to compromise an asset and how long it takes the defender to discover this”. To quote the DBIR: “the bad guys seldom need days to get their job done, while the good guys rarely manage to get theirs done in a month of Sundays.” Hey ho, we just have to keep plugging at it...
What next?
Well, I hope this summary will encourage you to read the full report, as you will find many other hidden gems in there. Also, apart from Cyber Espionage on page 39, none of the 8 other attack patterns will show the details of victim country (I have suggested this on a number of occasions, so maybe someday...) and I believe this would be particularly interesting to spot the differences once we overlay socio-economic conditions and technology considerations in the various countries (or groups thereof). I also believe it would be nice to have some analysis (or at least data) on breaches or incidents that resulted directly from lack of security at third parties (partners) in the supply chain of any given business (e.g. like in the Target breach). The DBIR still only gives information on partners where they are the threat actors (i.e. they perpetrate the breach, see page 8). Given the increased focus on supply chain management in various regulations worldwide, this would be a nice addition...
Thanks again to the Verizon DBIR team for an excellent report!
Until next time...
neirajones



No comments:
Post a Comment